Introduction to Dam Breach Modeling using HEC-RAS
Disclaimer: This post is a simple introduction to dam breach modeling using HEC-RAS. A H&H modeler should not perform a dam breach modeling task without consulting experienced H&H and geotechnical engineers or dam owners. Any dam breach analysis should be done by following the required state or federal guidelines such as USACE HEC TD-39, FERC Engineering Guidelines Dam Breach Analysis, Prediction of Embankment Dam Breach Parameters, or Oklahoma Dam H&H Guidelines.
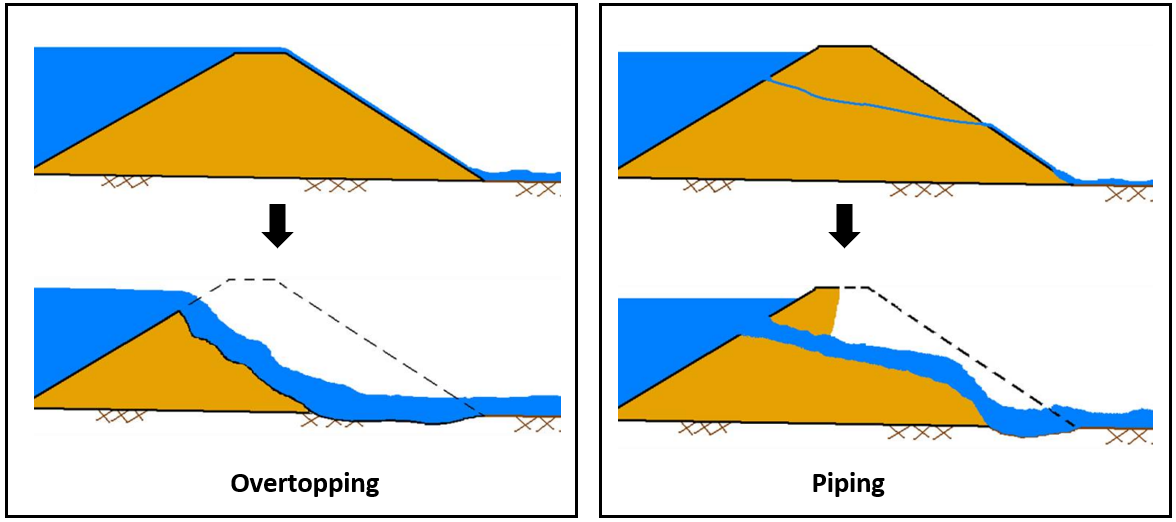
A dam breach (or dam break) analysis is often required by federal or state regulations to evaluate the potential risk to downstream properties and populations, prepare Emergency Action Plan (EAP), or understand what a warning time is. Among several different dam failure mechanisms, overtopping and piping are the two most common ones roughly accounting for 60%~70% of all dam failures (Figure 1).
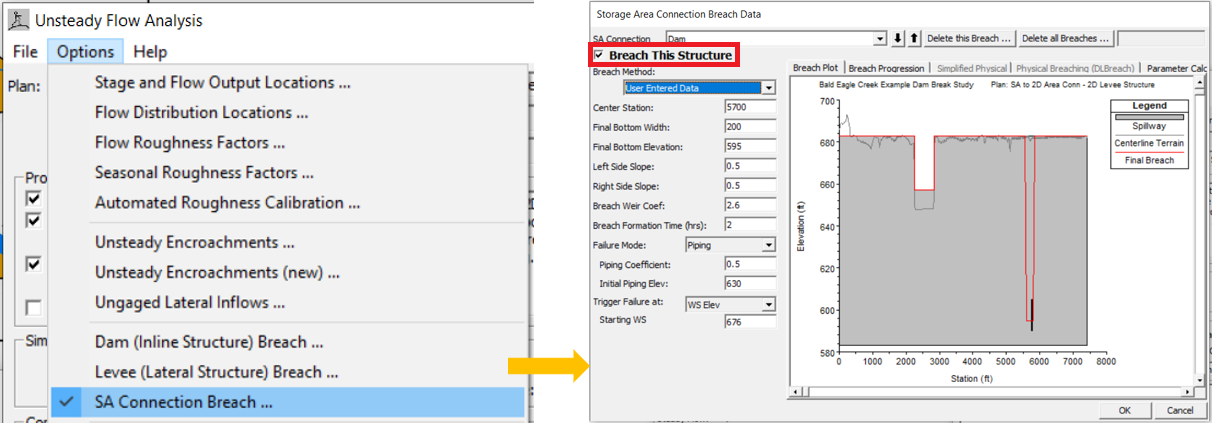
A dam/spillway in HEC-RAS is usually represented by an inline structure or a SA/2D connection or even a lateral structure, and to breach it, click to open one of the breach data editor windows from Options menu of Unsteady Flow Analysis (Figure 2). The breach location, size (dimension and elevation), and breach development time are the three most important factors of determining outflow hydrographs and downstream inundation. It is crucial to consult with dam experts, geotechnical engineers, and dam owners when estimating these parameters for a dam breach analysis. Additionally, the parameter sensitivity analysis should always be performed whenever it is possible.
Currently in HEC-RAS three breach methods are available: user entered data, simplified physical, and physical breaching (DLBreach). This post is to focus on the user entered data method which requires a modeler to type in all of the breach information (Figure 3).
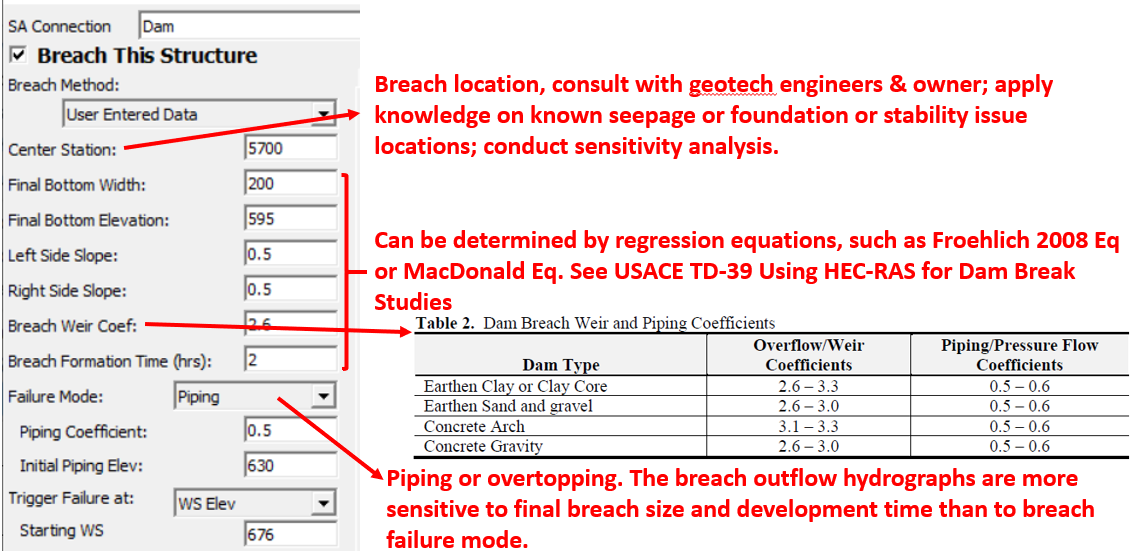
For a dam breach analysis (Inline Structure or SA/2D Connection), since the reservoir/lake usually is modeled as a storage area with one single WS (water surface) upstream of the dam, the breach location is really not that important; however, for a lateral structural (levee) breach analysis, because WS varies at different locations along the lateral structure, the breach location must be selected carefully (the triggering WS is read from the breach location station).
HEC-RAS has coded in several regression equations in breach data editor window to help a modeler to estimate the required breach geometric and timing data (Figure 4). Among the five regression equations, MacDonald et al Equation and Froehlich Equations are the most common ones. Oklahoma Water Resources Board recommends using Froehlich Equations for earthen dam breach analysis since Froehlich Equation results have a better match with the historical dam failure database and the physically-based erosion model NWS-BREACH than other regression equations.
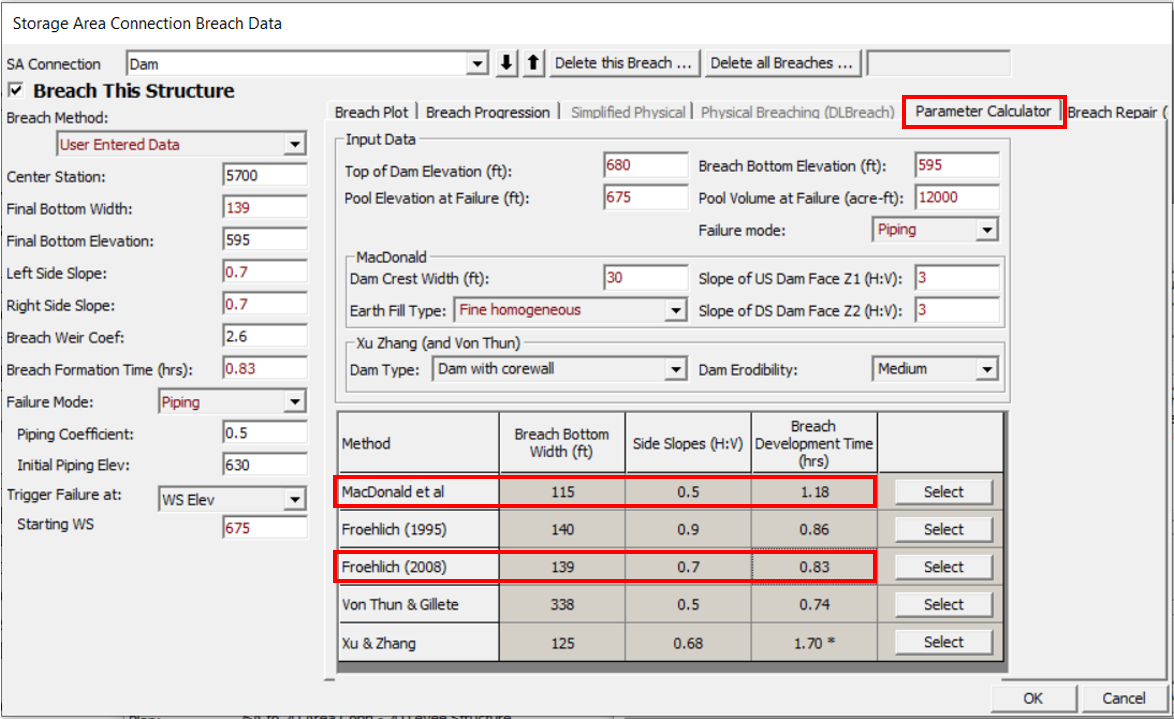
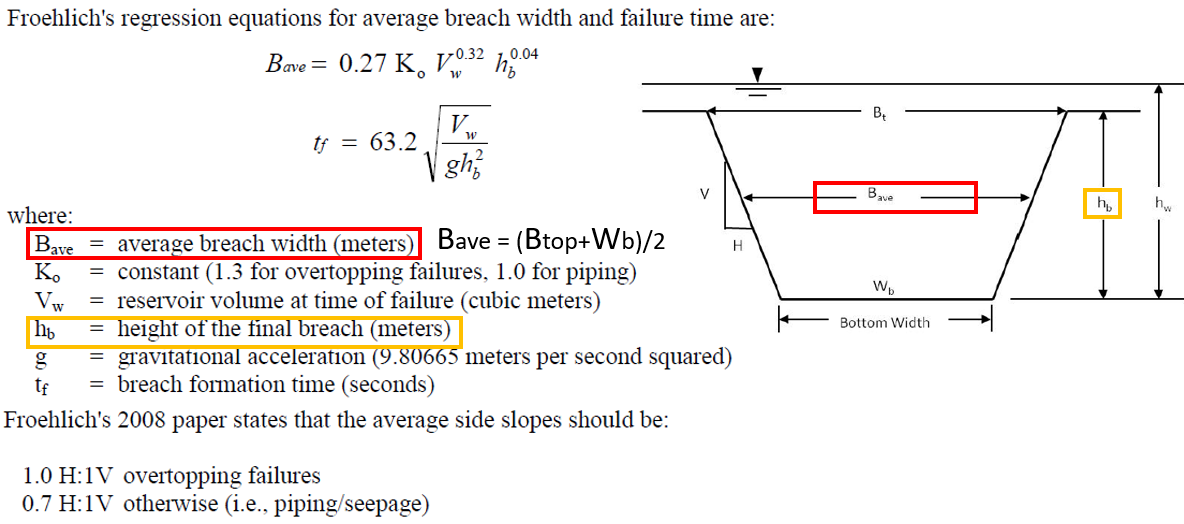
Froehlich 2008 Equation (Figure 5) is a slight improvement from its 1995 version, and it can be utilized to estimate average breach width and breach formation time. The breach bottom width can easily be calculated from the average breach width with known breach side slopes and heights. Froehlich assumes that a breach height is the elevation difference between dam top and natural ground elevation at the breach location.
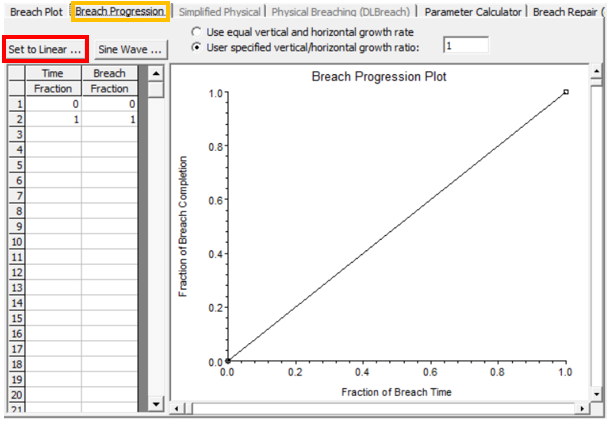
The breach formation time alone is not enough to decide what a breach geometry size is at each time step. HEC-RAS has two breach progression methods (temporal development distribution): Sine Wave (Figure 6) and Linear (Figure 7). Sine Wave breach progression method assumes a breach develops slowly at the start and the end during a breach formation.

A dam breach model should be extended sufficiently downstream to cover all the areas that are likely to be significantly impacted by a breach. Several options are explained in this post to determine an appropriate downstream boundary location.
When running a dam breach analysis in HEC-RAS, a smaller time step (10 seconds, 5 seconds, or 2 seconds or even less) is usually required due to rapid rising and recession limbs of an breach outflow hydrographs.
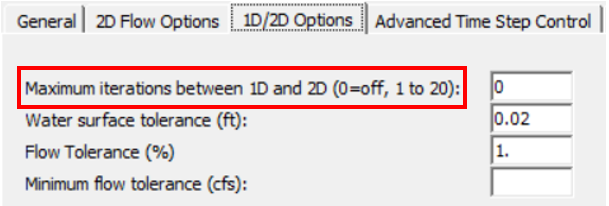
Other methods to stabilize a dam breach unsteady model include increasing lateral or inline structure stability factor/weir or gate flow submergence decay exponent (Figure 8) from default 1.0 to 2.0 or 3.0. Turning on iterations between 1D and 2D (Figure 9) is another option to stabilize a model, but it is usually not recommended unless it is absolutely necessary.

When HEC-RAS 2D is used for a dam breach analysis, Shallow Water Equation (SWE) is preferred over Diffusion Wave Equation as the 2D solver (Figure 10).

1 COMMENT